Cyber Threat Intelligence
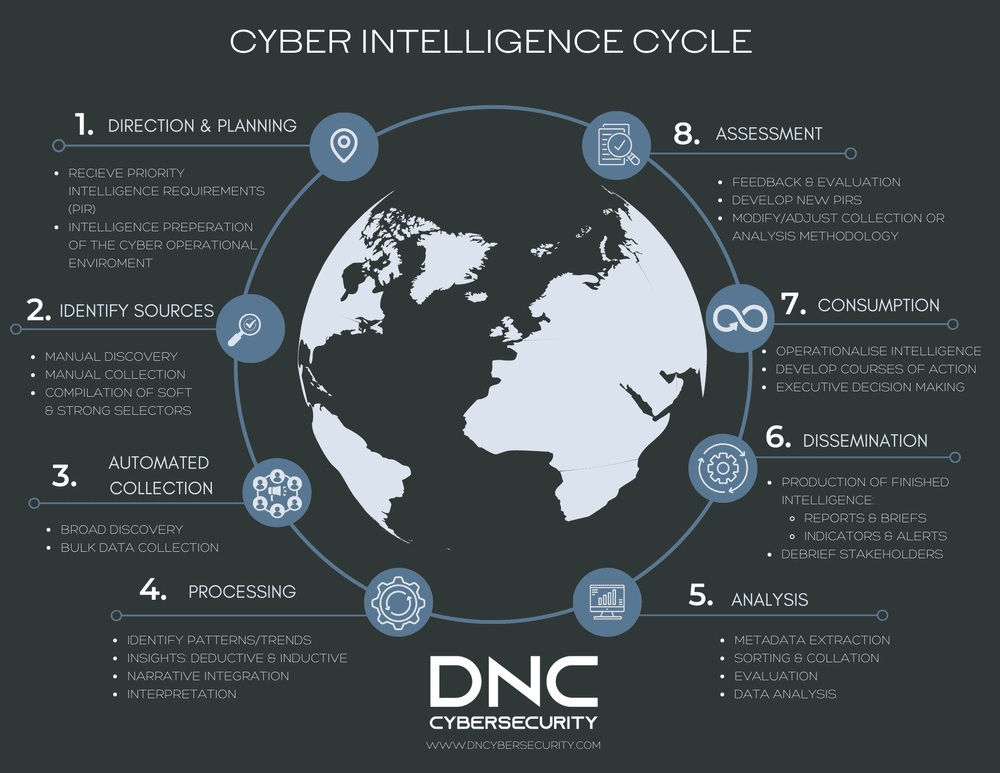
What we aim to achieve with this article, is to share specific ways that cyber intelligence analytical techniques and collection methods can be integrated into broader intelligence processes. We therefore present a more structured approach to cyber intelligence collection, processing, analysis and dissemination. The cyber intelligence dimension to each phase of the intelligence lifecycle is discussed and potential benefits explored.
Cyber Threat Intelligence Read More »