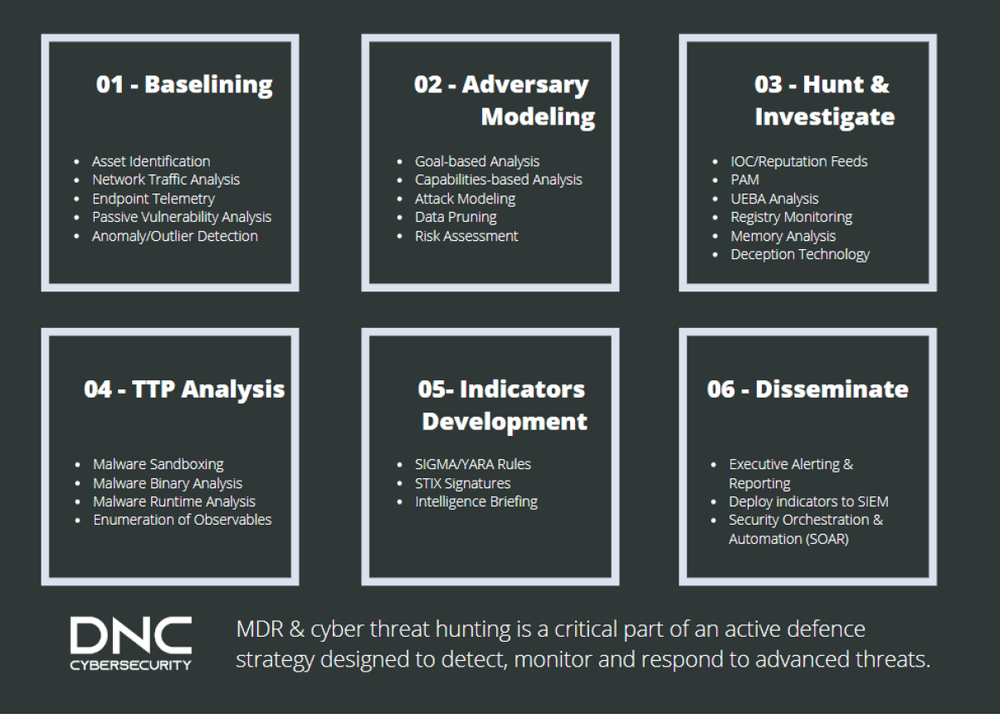
Cyber threat hunting is a critical part of an active defense strategy designed to detect, monitor and respond to advanced persistent threats
John Daniele, Managing Director, DNC Cybersecurity
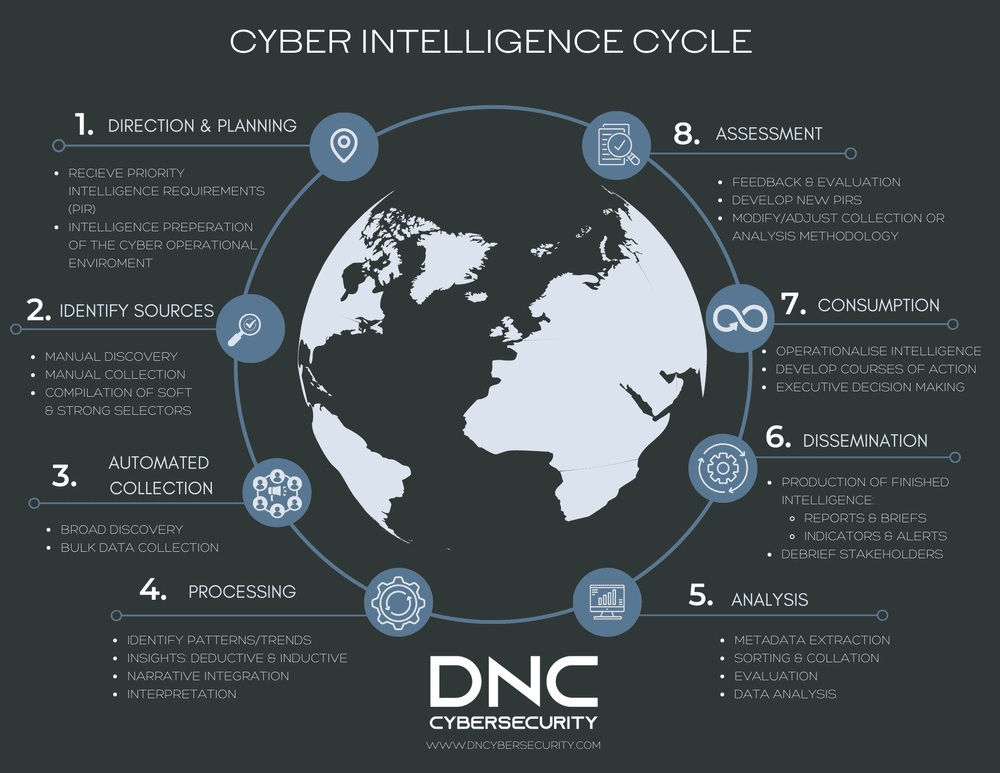
Cyber threat hunting is a proactive strategy to detect threats that evade traditional approaches to security operations. Threat hunting involves the systematic and continuous searching of networks and endpoints, for anomalies and outliers that indicate threat activity. Instead of relying solely upon automated detection mechanisms, which rely upon more passive means of identifying threats, threat hunting applies a more agile strategy to root out cyber adversaries that are hidden within your business environment.
Why Threat Hunting?
Cyber threat hunting is designed to address the shortcomings of automated approaches to ransomware and advanced persistent threat detection, namely:
- SIEM based signature detection does not scale well with rapidly emerging threats
- Threat intelligence feed data quality is often poor and unmanaged feeds are prone to excessive false positives and false negatives
- Indicators of Compromise (IOCs) do not address the unique threat profile of an organization, nor do common IOCs indicate the capabilities and resources of that organization’s most likely adversaries
Our threat hunting methodology begins with the deployment of tools into a target environment to gain the most visibility and observability into active threats. During this process, our team will work with the customer to identify its most valuable assets and perform an “attack trees” analysis to discover the attack paths a determined adversary might use. At these junctions, we will deploy additional network security monitoring and endpoint detection and response tools and technologies to capture and observe threat activity and related behaviours. Once we have “prepped” our digital battlefield, we then employ a structured methodology to threat hunting as documented within the chart below.
If your organization is struggling to gain visibility into emerging ransomware threats or suspect that you have been breached, we would be happy to engage with your team and help provide the necessary cyber threat hunting and digital forensics and incident response support and assistance to bolster your organization’s active defense strategy.