managed detection for small business
Managed Detection & Response
The pace and sophistication of cyber attacks is ever increasing. In the absence of strong security measures, this trend poses serious risks to small and medium-sized enterprises that are exposed to cyber criminals.
Talk to us today about protecting your business:
Overview
A sensible approach to managed cybersecurity
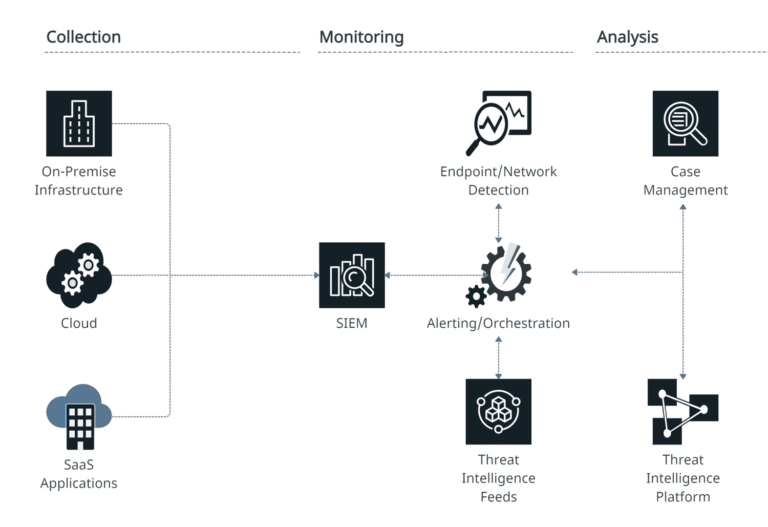
Our Managed Detection & Response (MDR) solution is intended to augment your investment in existing security technologies such as firewalls, antivirus and intrusion detection systems by providing continuous monitoring and automated security response.
Our team provides a more proactive approach to security through the use of structured and unstructured threat hunting methods to detect threat actors before they impact your business operations. Our MDR enables your organization with the observability it needs to keep your digital assets safe, so that you can better focus on core business activities that generate value.
We offer a cloud based threat detection and response capability that’s designed to meet the needs of small and medium-sized enterprises.
Flexible Service Tiers
We offer a flexible, tiered solution that can be tailored to meet your cybersecurity needs and budget.
Our compliance tier is ideally suited to organizations that have a limited number of log sources and simply need an automated approach to threat detection to augment existing capabilities. Our MDR infrastructure can help enrich incoming events with threat intelligence and raise alerts to the organization’s existing security team to triage and investigate.
Organizations with a more complex threat profile that need access to a team of cybersecurity operators to handle daily security triage and threat hunting responsibilities are better suited to our hunt tier. Our operators can provide more contextualized reporting of security incidents or deliver consultative guidance and direction on a 24×7 or 8×7 basis depending on budget and needs. In this tier, our operators will spend the time to learn the intricacies of your infrastructure and operations and devise a daily hunting protocol to uncover relevant threats. For more information about our threat hunting methodology, be sure to check out our insights blog article here.
In addition to managing daily cybersecurity operations, our team can also provide incident response support for all high severity incidents that occur within your environment. Organizations that require digital forensics support to mitigate the impacts of ransomware attacks, investigate cyber breach incidents or respond to a live attack can also retain our team on a managed services basis.
Organizations that are exposed to sophisticated threat actors or advanced persistent threats need actionable insights to pre-emptively defend their environments. In this tier our team will also provide a complete managed threat intelligence solution. Beyond the integration of commodity threat feeds, our intelligence analysts will curate technical and analytical intelligence that are relevant to your industry and business. We do this by profiling the threat actors that are common to your industry sector. We will examine their prior operations and campaigns to derive an understanding of their tooling, tactics, techniques and procedures (TTP) and proactively monitor their activities before they target your business. In this tier, our team can crawl common underground and dark markets to identify leaked corporate data, credentials or compromised assets belonging to your organization. We can also monitor domain assets and online infrastructure for possible threats. Our intelligence reports can be consumed by both technical and executive stakeholders alike.
cloud-based detection & response platform
Our platform and services democratize access to sophisticated capabilities for small and medium sized businesses.